LLM Shielding for Cloud Apps: Extending Phishing Protection to Slack, Teams, and More

As businesses rely on collaboration tools like Slack and Microsoft Teams for day-to-day communication, cybercriminals have followed suit. In these cloud apps, employees tend to trust that messages come from genuine colleagues or partners, making it fertile ground for scams. Unlike with email – where most of us have learned to be wary of strange senders – a chat from a coworker on Slack or Teams doesn’t usually set off the same alarms. This implicit trust in internal messaging platforms is exactly what attackers are exploiting.
At the same time, Large Language Models (LLMs) are changing the game on both sides. Attackers are using AI to craft more convincing phishing lures, while defenders are beginning to deploy AI to detect and block these threats. In this blog, we’ll explore how LLM shielding can extend phishing protection beyond email to cloud collaboration apps – keeping Slack, Teams, and more secure from the next generation of social engineering.
The New Phishing Frontier: Slack, Teams, and Beyond
Slack and Teams have become indispensable in the modern workplace. Slack boasts tens of millions of users and is used by 77 of the Fortune 100 companies, while Microsoft Teams has hundreds of millions of active users. These platforms were originally walled gardens for internal communication, ostensibly safe from outside spam and phishing. In fact, Slack’s own site boldly claims “Unlike email, Slack is not susceptible to spam or phishing” because you only receive messages from your organization or trusted partners.
So, what changed? In recent years, Slack and Teams introduced ways to communicate with external parties. Slack launched Slack Connect in 2020, allowing cross-company channels and DMs, and Microsoft enabled external access and cross-tenant chats in Teams in 2022. These features are great for business collaboration – you can chat with clients, contractors, or partners in real time – but they massively increase the attack surface for phishing on these platforms. Now, a clever attacker can send a malicious message or invite that reaches your employees through Slack or Teams, even if they’re not in your company.
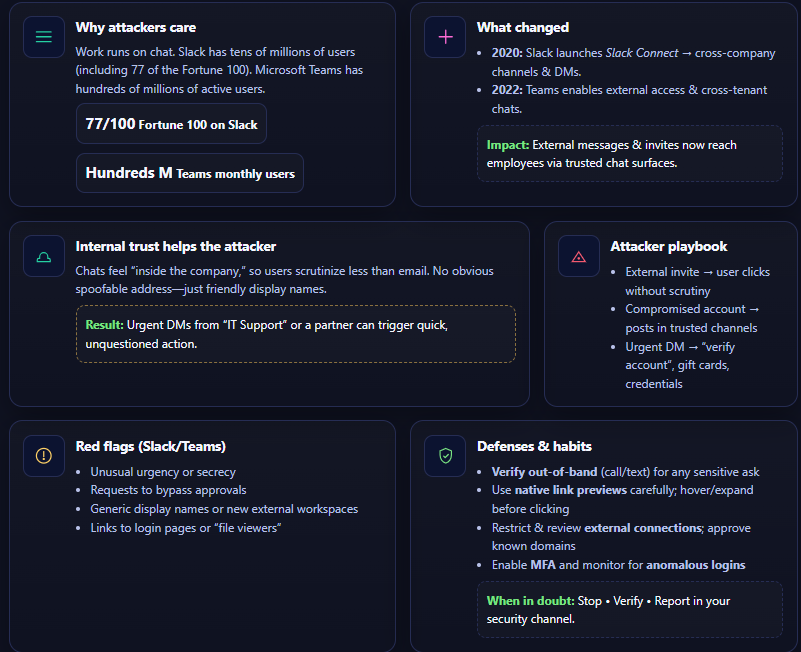
Moreover, internal trust works in the attacker’s favor. Employees aren't used to scrutinizing Slack messages like they do emails. There’s no spoofable email address visible, and everyone appears as a friendly display name. As one security expert put it, “we trust these programs implicitly” compared to email. Attackers know that if they can infiltrate these chats – through a compromised account or a convincing external invite – their messages will carry a sheen of legitimacy.
This trust, combined with the real-time, urgent nature of chat, means people are more likely to react quickly and less likely to double-check a request. Slack messages feel informal and immediate, so an urgent DM from “IT Support” asking you to verify your account can prompt quick compliance in a way an email might not. In short, Slack and Teams are the new phishing frontier for adversaries.
Why Attackers Target Slack and Teams
Several factors make Slack, Teams, and similar cloud apps attractive to phishers:
- Widespread Usage: These platforms are pervasive in enterprises. Attackers go where the people are. Microsoft Teams alone had about 270 million users as of 2022, and Slack usage continues to grow globally. A successful trick on these platforms can reach deep into an organization.
- Implicit Trust: As noted, users tend to trust internal messages more. An incoming Slack DM doesn’t trigger the same skepticism as an unsolicited email from an unknown address. This trust can be exploited – especially if the attacker poses as a coworker or a known external partner.
- Lack of Traditional Security Filters: Email has decades of security solutions built around it – spam filters, secure email gateways, DMARC/SPF checks for spoofing, etc. In contrast, Slack/Teams have fewer “gatekeepers.” There’s typically no built-in content filtering or phishing banner warning on a Slack message by default. As a Push Security analysis highlighted, instant messenger platforms “lack centralized security gateways and other security controls common to email”. There’s also no concept of “junk folder” in Slack; messages just arrive.
- External Entry Points: Features like Slack Connect and Teams guest access let outsiders in. An attacker can send a Slack Connect invite posing as, say, “John from TrustedPartner Inc.” If an employee accepts, the attacker now has a direct line to message them (and possibly other channel members) with malicious content. It’s hard for users to tell legitimate external contacts from fake ones in an invite – the attacker can choose any display name and organization name, making the request look business-relevant. Curiosity can get the better of the target (“I wonder what message this external person wants to send me?”), leading them to click “Accept”. Once inside, the attacker can impersonate others or drop phishing links under the guise of a new partner introduction.
- Urgency and Informality: Chat platforms create a sense of immediacy. People often respond in real-time and feel pressure to act quickly. Attackers abuse this by crafting urgent requests. For example, a scammer might DM an employee: “@Dave We have a security incident, I need your help now – send me the 2FA code you just got!” The casual tone and @mention make it feel like a quick ask from a colleague. Combined with the “always-on” culture of chat, this urgency can lower users’ guard. In many cases, employees react first and think later.
All these factors mean Slack/Teams phishing attempts have a higher chance of slipping past both technical defenses and human skepticism. And indeed, we’re seeing that happen.
Real Incidents: From Slack Scams to Teams Takeovers
If all this sounds a bit theoretical, consider some real-world incidents that show how attackers are breaching organizations via Slack and Teams:
- Scattered Spider’s Internal Chat Infiltration: In mid-2025, cybersecurity agencies warned that the Scattered Spider hacking group was infiltrating Microsoft Teams and Slack to phish employees. These attackers didn’t bother with email at all – they jumped straight into the company’s own chat channels. By posing as IT support or other trusted personas, they manipulated people into revealing credentials or approving multifactor authentication prompts. Once in, they used the foothold to spread malware and escalate privileges. The FBI noted how this group exploited the trust in internal messages to “quietly gather intelligence, escalate privileges, or manipulate users into taking harmful actions”. In other words, they turned Slack/Teams into hunting grounds.
- Deepfake CEO on Teams: In a sophisticated 2022 attack, a CEO was deepfaked to trick employees via a Teams meeting. As reported by security researchers, attackers scraped a video of the CEO from a public interview and then posed as him on a live Teams call. They even added a fake background (showing he was abroad on business) to sell the illusion. During the short call (with conveniently “broken” audio), the fake CEO dropped a SharePoint link in the Teams chat, asking the employees to upload some sensitive documents. One employee clicked – fortunately, they were blocked from accessing the malicious page in that case. This incident shows how far attackers will go: combining social engineering with multimedia AI fakery to breach organizations. If a video call from your boss can be faked, a simple text chat from a colleague can certainly be faked too.
- Malware in Microsoft Teams Chats: In early 2022, researchers from Avanan (a security firm) discovered that attackers were dropping malware files into Teams conversations at an alarming rate. They observed “thousands of attacks” where a hacker in a compromised Teams account attached a malicious .exe file in chats. Because it’s coming through Teams – a trusted channel – users were more likely to click it. The .exe would then install a Trojan and ultimately deploy malware on the victim’s computer. Teams didn’t have the same level of file scanning for malware that email attachments might have, so these slipped through. As Avanan noted, “end-users have an inherent trust of the platform”, which the hackers exploited to run their payloads.
- Business Email Compromise Moving to Chat: Classic BEC (Business Email Compromise) scams have started to appear on Slack/Teams. In a BEC scam, attackers impersonate a high-level exec or partner and try to convince someone in finance to transfer money or reveal sensitive info. Traditionally this is via carefully crafted emails. Now, attackers expand those tactics into chat apps – which some researchers dub “the new BEC”. For example, a fraudster might send a Teams message pretending to be the CFO: “Hey, I’m in a meeting, need you to urgently process a payment. Are you at your desk?” If the target isn’t careful, the conversation can move fast and bypass the usual email checks. Sophos researchers observed that as businesses shift to cloud collaboration, attackers follow suit: “legitimate hosted services – like Microsoft Teams and Slack – will be an attractive avenue for attackers”.
These cases underscore a key point: phishing has expanded well beyond email. In fact, recent analyses estimate that roughly 40% of phishing campaigns now target channels outside of email – such as Slack, Teams, or social media messages. The enemy is already at the (chat) door. So how do we defend these channels?
The Challenge: Why Traditional Defenses Fall Short
Defending Slack and Teams from phishing is a new challenge for many security teams. Relying on the same tools and training used for email isn’t enough, for several reasons:
- Lack of Built-in Filters: As mentioned, Slack/Teams messages aren’t run through robust spam or phishing filters by default. An email gateway might block a known malicious link or flag a suspicious domain, but a Slack message with that same link could sail straight through to the user. Some enterprise plans and third-party tools can add scanning (more on that soon), but many organizations haven’t deployed those yet.
- User Unfamiliarity: Employees have been drilled for years on how to spot phishing emails (check the sender address, look for misspellings, etc.). But phishing via chat is less familiar. People might not know to verify a Slack invite or question a DM asking for credentials. Attackers exploit this learning gap.
- Spoofing and Impersonation: Slack and Teams can display names and profile pics that look official. Attackers may not be able to “spoof” an internal username exactly (especially on Slack, external users get a little badge or different name style), but they can create very close lookalikes. For instance, an external Slack account named “IT Support (Ext)” could still fool someone who doesn’t notice the tiny indicator that it’s external. In Teams, a compromised partner tenant could appear as a trusted contact. There aren’t straightforward indicators like email headers, so detecting imposters is tricky without specialized tools.
- Limited Admin Controls for Content: Admins can restrict external access to some degree (e.g., only allow Slack Connect with approved domains). However, many companies enable these features to facilitate business, and not all have strict allow-lists. Monitoring content in real-time is also hard – you’re not going to manually read people’s Slack chats, and privacy concerns loom. So, automated detection is needed, but legacy DLP (data loss prevention) or keyword-based approaches often produce too many false alarms in the free-flowing chat context.
- Legacy Tools Lack Context: Traditional security tools work on known bad signatures or simple rules. They struggle with the nuanced, contextual nature of chat messages. An email filter might flag “wire transfer” keywords, but in Slack, casual language like “can you quickly send over that file?” might be the only clue of a phishing attempt. The legacy tool doesn’t understand conversation context – like whether such a request is normal between those users. It has no semantic awareness. In fact, this is a problem even in email: older filters don’t truly “read” the message for meaning. They can’t tell if “As per our Zoom call, please review the attached doc” is fishy because they don’t know no Zoom call happened. This gap is even more glaring in chat, where context (who is speaking, what’s been discussed before) is key to judging legitimacy.
Given these challenges, it’s clear we need a new approach. Enter AI and LLMs as a defensive shield.
Attackers Are Using AI – So Should We
Before diving into how defenders can use LLMs, it’s worth noting that attackers themselves are leveraging AI to make their phish more effective. Gone are the days of broken English and obvious tells. Today’s phishing messages can be polished and perfectly tailored, often generated or assisted by AI.
Attackers feed contextual data into LLMs to produce extremely convincing content. They might gather details from LinkedIn, company press releases, or previous communications, and then prompt the AI to compose a message weaving those details in. The result? A phishing DM or email that sounds like an insider wrote it. For example, an AI could generate a Slack message from “HR” referencing a real corporate event (“As discussed in the All-Hands yesterday, please fill out the attached survey”) when no such request was actually authorized. These messages lack the usual red flags and have context that disarms skepticism.
AI can also mimic writing style. A well-tuned model might produce text in the style of your CEO’s brief chats, or your coworker’s informal tone. It might even vary the phrasing to avoid repetition, making it read more human. Attackers have begun to use these LLM-written phishes at scale. In fact, Microsoft observed that some threat actors “are turning to language models to facilitate their objectives” in social engineering campaigns. When you get a perfectly worded request that feels legit, it very well might have been machine-crafted.
This all sounds pretty scary – and it is a challenge – but there’s a flip side. The same capabilities of LLMs that make them great mimics can be harnessed by defenders to detect those subtle signs of fraud. Essentially, it takes an AI to catch an AI (or an AI-assisted human). Security teams are now deploying LLM-based systems to sift the real from the fake in communications.
What Is LLM Shielding for Cloud Apps?
LLM shielding means using large language model technology as a protective layer to analyze and filter communications in cloud apps. Instead of relying on simple blocklists or rigid rules, an AI model “reads” messages much like a human analyst would – but at machine speed and scale. Here’s how LLM-powered protection can work for Slack, Teams, and similar platforms:
- Natural Language Understanding: The AI doesn’t just scan for bad links; it actually interprets the text. It can identify if a message is attempting to obtain sensitive info or induce an unusual action. For example, a message like “I lost access to the client database, can you send me the backup files?” might be benign or malicious depending on context. An LLM can evaluate the phrasing, the roles of sender/receiver, and past interactions to judge intent. It understands semantic cues like urgency, requests for credentials, or tone mismatches.
- Anomaly Detection in Style and Behavior: By learning how your users typically communicate, an AI shield can flag when something’s off. If Bob from Engineering suddenly writes in a very formal way on Teams (not his usual style), or uses phrases he’s never used before, an LLM-based system can pick up on that deviation. It’s similar to how we humans might think “this message doesn’t sound like Bob.” The AI can compare against known patterns (without violating privacy – it looks at metadata and stylometry, not reading private info aloud) and assign a risk score. This is incredibly useful for catching compromised accounts. If an attacker is controlling an employee’s Slack account and messaging others, their writing style or timing might differ enough for AI to notice (e.g., the attacker writes all grammatically correct English whereas the real user often uses slang and emojis).
- Context Awareness Across Channels: LLM shields can correlate information beyond a single message. For instance, if a phishing email was sent to an employee and an hour later a Slack message comes with a similar request, an AI system can connect those dots. It treats Slack, Teams, email, etc. as part of one big communication context. Microsoft has hinted at this kind of approach in their security solutions – using AI to parse language and “identify attacker intent” across collaboration channels. The AI can remember that no, Bob and Alice didn’t have a Zoom call earlier even if a message claims “as we discussed on Zoom...”, because it has some knowledge of normal events or can check the calendar context if integrated.
- Real-Time Link and File Analysis: Beyond text, an LLM-based guard can also help analyze links and files on the fly. Traditional link scanners check a URL against blacklists or open it in a sandbox. An LLM enhancer could read the content of a linked page and assess if it’s likely a phishing login page. For example, if you click a Slack link that leads to a site that looks like a Microsoft 365 login, an AI could notice the branding and language on that page and flag it as suspicious (“this site is imitating a login page for Microsoft, but the URL is weird”). Similarly, if a PDF or document is shared, future AI might read it to ensure it’s not a malicious form or known scam document.
- User Warnings and Guidance: The goal is not just silent blocking. LLM shielding can be set to warn users in context. Imagine an AI assistant built into Slack that pops up saying, “This message looks suspicious – the sender is asking for credentials and the tone is unusual. Are you sure you trust this request?” Such a nudge, phrased in a helpful way, can prompt users to think twice. Because it’s AI-driven, it can be conversational and explain the reason (unlike a vague “This message is flagged” banner). Some advanced security platforms already offer this kind of Slack/Teams chatbot that educates users when something is detected.
- Continuous Learning: The beauty of using LLMs is that they can learn and adapt. They get better as they see more examples of phishing attempts, especially AI-generated ones. If attackers shift tactics, the model can incorporate those patterns (either through retraining or few-shot learning on the fly). This predictive element means we’re not just matching yesterday’s threats. We’re equipping our defenses to catch novel, clever scams that haven’t been seen before – exactly where static rules fail.
In essence, LLM shielding brings a human-like intuition to automated defense. It’s as if you had an expert security analyst reading every Slack message and Teams chat 24/7, instantly alerting or intervening when something smells phishy – except it’s AI doing the heavy lifting at scale.
How LLM-Powered Protection Integrates with Slack and Teams
You might wonder, how do we actually deploy an AI shield in our chat apps? The good news is, you don’t need to build this from scratch. There are emerging solutions and integrations designed to bring AI into your cloud app security. Here are a few ways organizations are implementing LLM-based phishing protection for Slack, Teams, and others:
- Native Security Integrations: Microsoft’s security stack (Defender for Office 365, Defender for Cloud Apps) has been evolving to cover more than just email. For example, Microsoft Defender for Cloud Apps can connect to Slack Enterprise via API to monitor for threats. It detects things like anomalous account behavior, suspicious file sharing, or unusual login patterns in Slack. While Microsoft’s tools use a variety of detection methods (not all LLM-based), Microsoft did announce at Ignite 2025 that they now use purpose-built LLMs at scale to provide AI-powered email and collaboration security, hitting impressive detection accuracy. In practice, this means the same AI that scans your Exchange mailbox for a fake CEO email will also watch your Teams for that sort of BEC attack. These big tech solutions often work behind the scenes once connected – pulling chat data (with permission) and analyzing it in the cloud.
- Third-Party Security Bots and Connectors: Several security vendors have developed API-based connectors or bots for Slack/Teams that bring phishing protection directly into those platforms. They work kind of like a firewall for your chat. For instance, some solutions have a bot user that is added to channels and can scan messages in real time. If someone posts a link, the bot checks it; if someone gets a DM that looks sketchy, the bot can DM back or tag the user with a warning. As one guide notes, “some security platforms offer connectors or agents that can scan messages in Slack or Teams and warn users”. These connectors leverage AI on the backend to decide what to warn about. The advantage is they integrate at the application layer – no complicated network changes – and can often be deployed quickly via app marketplaces or admin settings.
- Cloud App Policies with AI triggers: Using CASBs (Cloud Access Security Brokers) or similar, companies are writing policies that incorporate AI. For example, you might have a rule: “Alert if message contains a link and AI risk score > 7/10.” The AI provides the scoring, and the policy engine handles the enforcement (alert, block, or quarantine). This layered approach ensures that even if the AI isn’t 100% certain, it can flag things for human review without outright blocking business communication.
- LLM-Powered Email Security extending to Chat: Companies that built LLM-based email security (to fight AI-crafted phishing emails) are extending their tech to other platforms. One example is StrongestLayer’s Cloud App Protection – an AI-driven solution originally for email that now integrates with collaboration apps via API. (Their approach doesn’t require fiddling with MX records or gateways; it plugs in via APIs to Microsoft 365, Google, Slack, etc., making it cloud-native and seamless.) Such a system uses the same LLM engine that reads emails to also read Slack messages, apply intent analysis, and then either warn the user or notify security teams if something looks malicious. The benefit is a unified AI brain watching all channels.
- In-House AI Bots: Some larger enterprises with AI expertise are even experimenting with building their own AI-powered Slack bots for security. For instance, an open-source project (Kyler’s Slack/Teams chatbot) was mentioned in a security newsletter as a way to deploy a terraformable Slack/Teams AI chatbot for experimentation. These custom bots can be tuned to a company’s specific needs, though maintaining one’s own AI model and keeping it updated on threat patterns is non-trivial. Most organizations will opt for a vendor solution due to the complexity.
No matter the method, the key is that these AI integrations act like a shield: they monitor communications in real time and enforce security without relying on humans to spot every phish. They strive to only intervene when necessary – the best ones have low false-positive rates, so users aren’t bombarded with warnings for every joke or odd message (nothing kills adoption of a security tool faster than constant annoying false alarms). It’s a fine balance: be vigilant but not disruptive, and LLMs, with their deeper understanding of language, are making it possible to achieve that balance.
Benefits of LLM Shielding in Collaboration Platforms
Deploying LLM-based phishing protection for Slack, Teams, and other cloud apps offers several clear benefits:
- Stops Advanced Threats Early: The biggest benefit is obviously preventing breaches. AI-driven filters can catch those sneaky attacks that legacy tools and untrained eyes would miss – whether it’s a well-disguised phishing link, an AI-written imposter message, or an unusual file share. By extending protection to chat and collaboration apps, you close a major gap. This can thwart attack campaigns in their initial stages, before an attacker steals credentials or plants malware. Think of it as covering the new backdoor that attackers were using to bypass your email security.
- Reduces Human Error: Even well-trained employees can slip up, especially on chat where things move fast. LLM shielding is like giving each employee a personal security advisor that whispers in their ear, “hey, something’s off about this message.” It provides a safety net for when humans are distracted, stressed, or just unfamiliar with a new type of scam. By catching what humans overlook, it dramatically lowers the risk of one unlucky click spiraling into a breach.
- Understands Context Better (Fewer False Alarms): Traditional keyword-based alerts in chat can go wild – flagging harmless phrases or everyday file transfers as threats. LLM-based systems understand context, so they can discern benign situations from malicious ones more accurately. For example, they can tell the difference between “here’s the link you asked for” in a normal workflow versus the same phrase coming from an unusual source at an odd time. This context awareness means alerts are more relevant, and users/admins don’t waste time on false positives. When an AI alert does pop up, employees are more likely to take it seriously because it’s not crying wolf constantly.
- Seamless User Experience: The ideal security is almost invisible until needed. LLM shields integrated into Slack or Teams operate in the background. They don’t slow down your messages or require cumbersome steps. When they do intervene (blocking a link or warning about a message), it can be done within the app – e.g., the user sees a warning banner or a bot message. This keeps the workflow smooth. Compare this to, say, an email quarantine where a user has to go to a separate portal to check if a mail is safe – chat security with AI can be much more user-friendly. A great example is using a friendly chatbot that educates users at the teachable moment (when they almost clicked something bad), turning security into a learning moment rather than just a roadblock.
- Adaptable to New Threats: Because these defenses are AI-driven, they can adapt quickly as attackers change tactics. If a wave of Slack token theft scams emerges, the AI can be trained on those patterns and start catching them, even if the exact keywords or URLs differ each time. In one case, when a new phishing kit started dropping weirdly formatted links, an LLM was able to identify the intent of those messages (they were trying to get users to a fake login) even though the text wasn’t a known bad signature. This kind of adaptability is crucial as we head into an era of AI-versus-AI in cyberattacks.
- Holistic Security Posture: By extending protection to “all the places work happens” (email, chat, cloud apps), you create a unified shield around your organization. Attackers often try multiple channels – if email fails, they might try Slack, or vice versa. An LLM shield that spans channels can correlate signals and ensure there isn’t a weak link. It also simplifies the incident response: your security team gets alerts from one system that covers everything, instead of disparate tools for each app. This holistic view can reveal patterns (maybe the same attacker probed via email and Slack) that you’d miss if you only watched one platform.
In short, LLM shielding brings effectiveness and efficiency. It boosts security where it was previously thin, and it does so in an intelligent way that integrates well with how users work.
Beyond Slack and Teams: Other Cloud Apps to Secure
While Slack and Teams are our focus, they’re not the only apps that need attention. “Extending phishing protection to... More” means looking at all the cloud tools where your employees communicate and share. Phishing and social engineering can creep into any app where messages or content are exchanged:
- Workplace Social Networks: Platforms like Workplace by Facebook, Yammer, or even LinkedIn (for professional networking) can be avenues. LinkedIn messages, for instance, are commonly used to phish employees with job lures or collaboration scams. Attackers might send a malicious link as part of a LinkedIn conversation, knowing it won’t be scanned by corporate email filters. If your employees coordinate in a LinkedIn group or similar, that’s a vector.
- Project Management and Shared Drives: Ever get a fake Google Drive share email? Now imagine a fake notification on Slack or a malicious comment in a Google Doc. Tools like Google Workspace, Dropbox, Box, Monday.com, Asana, etc., involve sharing links and files – all can be abused. For example, a phisher might drop a Google Docs link in a chat channel, claiming “Here’s the doc we discussed.” The doc contains a phishing link in it or a comment tagging someone with a malicious URL. Or consider a Trello board comment that has a sketchy link. Your LLM shield should ideally cover these or the communications around them. Many phishing campaigns aim to steal cloud app credentials by imitating these share alerts.
- Video Conferencing and VoIP: Zoom and Webex have chat features and of course meeting invites. “Zoom phishing” became a term – attackers would send calendar invites or Slack messages with fake Zoom meeting links (really leading to credential phishing pages). Also, vishing (voice phishing) and deepfake audio can target via phone or voice messages. While an LLM can’t “listen” to a phone call (yet), if that voice scam is followed up or initiated via a chat (like “I just left you a voicemail, please do X”), a smart system can catch inconsistencies. AI is also being used to detect deepfake voices by analyzing audio patterns – a developing area complementary to what we discuss here.
- Customer Support and Ticketing Systems: Tools like Zendesk, Jira Service Desk, or internal helpdesk chats can be targeted. An attacker might impersonate a customer or an IT staff via a support channel to get info or access. Ensuring those systems have checks (and that agents are aware of phishing tricks through them) is part of a comprehensive defense.
The takeaway is that any cloud app that connects people can be leveraged in social engineering attacks. It’s a lot to cover, but the principles remain the same: apply intelligent monitoring and give users a safety net. We’re likely to see AI defenses expand into all these areas – some email security providers already advertise protection for OneDrive, SharePoint, Slack, etc., in one package.
For now, focusing on Slack and Teams will cover the highest-risk channels for most organizations, but keep an eye on those “and more” apps. Don’t let a crafty phisher find the one collaboration tool you forgot to secure.
Layered Defense: LLMs + Good Security Hygiene
While LLM shielding is a powerful new tool, it works best in tandem with other security best practices. Think of AI as adding a smart layer of defense – not the only layer. To truly secure your cloud apps, combine LLM-powered protection with these measures:
- Strong Authentication: Since many Slack/Teams attacks start with a compromised account, having phishing-resistant MFA (Multi-Factor Authentication) on all accounts is critical. Use methods like hardware security keys or biometric MFA which are much harder to bypass. That way, even if someone falls for a phish and gives up credentials, the attacker can’t easily reuse them to log into your Slack or Office 365.
- Access Controls: Limit who can create external Slack connections or who can receive external messages. If only certain teams need Slack Connect, restrict it for others. In Teams, you can allow external communications only with whitelisted domains for partners. The principle of least privilege should extend to collaboration apps too – for instance, not everyone should be able to invite external users into a channel.
- User Training for Chat Phishing: Update your security awareness training to include chat-based phishing scenarios. Employees should learn that if the CFO pings them on Teams out of the blue asking for a wire transfer, they need to verify via another channel. Encourage a culture where it’s okay to pause and verify an unusual chat request (e.g., call the person or use a known contact method). Show examples of Slack/Teams phishing messages in training so they know the red flags (like an external badge on a user name, or someone asking for login codes – which legitimate IT will never do over chat).
- Safe Collaboration Settings: Both Slack and Teams offer admin settings to enhance security. For example, Slack Enterprise Grid admins can disable public invite links, require approval for Slack Connect invites, and monitor workspace access logs. Microsoft Teams admins can turn off or tightly control guest access if not needed, and enable cloud app security monitoring as we discussed. Utilizing these settings creates a baseline of security so the AI doesn’t have to catch everything.
- Incident Response Plan: Have a plan for responding if an AI alert or any alert flags a potential compromise in Slack/Teams. This might include steps like removing any malicious messages (Slack admins can delete messages organization-wide), resetting the account that was taken over, informing the team of the incident (without causing panic), and reviewing logs to see what the attacker did. The faster you respond, the less damage an intruder can do if they do slip in. AI can even assist here by providing a quick summary of the attacker’s activity to responders.
- Continuous Monitoring and Improvement: Keep an eye on the metrics from your AI shield – how many incidents averted, false positives, etc. This can guide you to tweak sensitivity or provide targeted training. If you see many attempted Slack phishing invites being blocked, it’s a sign to remind your users about being cautious with external contacts. Also stay updated with threat intelligence: if a new Slack/Teams scam technique is trending (say, a fake “Slack Security” bot messaging users), make sure your defenses (and employees) know about it.
In summary, an LLM shield is a game-changing ally, but it’s part of a bigger security ecosystem. You still want strong locks on the doors (MFA, access control) and street-smart residents (trained users), even as you install that new high-tech security camera (AI monitoring).
Final Thoughts: Staying Ahead with AI-Powered Defense
Phishing in Slack, Teams, and other cloud apps is not a hypothetical threat on the horizon – it’s here now, and it’s growing. Attackers are opportunistic; they will exploit any channel where our guard is down. For a while, internal chat and collaboration tools were a blind spot, a soft underbelly of corporate security. We trusted these environments too much, and attackers took notice.
But we don’t have to cede this ground. By extending phishing protection into our cloud apps, especially using advanced AI techniques, we can catch up to the attackers and even get ahead. LLM shielding brings a level of insight and nuance to threat detection that matches the sophistication of modern attacks. It’s like having an expert linguist bodyguard for every digital conversation – one who never sleeps and never gets tired of checking messages.
The move to AI-powered defense is already happening. Microsoft’s massive scale deployment of LLMs for email and collaboration security is one testament. Innovative security startups are launching LLM-native solutions to tackle AI-powered phishing head-on. Early adopters are seeing the benefits in dramatically reduced successful phishing incidents and earlier detection of compromise. As these tools become more widespread, the cost-benefit equation for attackers will shift – sneaking into a Slack channel won’t be the low-hanging fruit it once was.
For organizations, the path forward is clear: bolster your human defenses with AI defenses. Educate your team about the new risks, lock down settings where you can, and deploy an LLM-based shield to cover the gaps. The goal is to make sure that whether a phishing attempt comes by email, chat, or carrier pigeon, it encounters intelligent resistance.
In an era where AI is weaponized by threat actors, we must weaponize AI for protection. Your Slack workspace and Teams environment can be just as well-guarded as your inbox – if you put the right shields in place. By embracing LLM shielding for cloud apps, you’re telling attackers: “Not so fast – our guard is up everywhere.” And that could make all the difference in outsmarting the next phishing plot before it hooks your business.
Stay safe, stay vigilant, and let AI help watch your back in every channel. With a smart combination of technology and training, we can continue to collaborate freely and fearlessly, even as the phishing landscape evolves.
Frequently Asked Questions (FAQs)
Q1: Can phishing attacks happen on Slack or Microsoft Teams?
Yes – unfortunately, phishing isn’t limited to email anymore. Cybercriminals have begun targeting chat apps like Slack and Teams by sending phony messages or malicious links. They bank on the fact that people often trust internal communications, hoping users will click without the same caution they’d use in email.
Q2: Why are attackers targeting Slack and Teams for phishing now?
Attackers go wherever people are communicating. As more work chats move from email into tools like Slack and Microsoft Teams, hackers see new opportunities. In fact, roughly 40% of phishing campaigns now extend beyond email into channels like Slack and Teams, catching people off-guard on these platforms that they consider “safe.”
Q3: What does a phishing attempt on Slack or Teams look like?
It often looks like a normal chat message – but with a malicious twist. An attacker might impersonate a co-worker or IT support and send you a direct message that seems urgent, asking you to “reset your password here” or to click an unexpected link. They exploit the casual nature of chat, hoping you won’t think twice about a request that would seem suspicious if it came via email.
Q4: How can AI help protect Slack and Teams from phishing?
AI (including large language models) can act like a smart shield for your chat apps. These systems analyze messages in context and can automatically flag or block anything that looks phishy or out of the ordinary. In fact, security experts recommend using intent-aware AI tools to monitor internal Slack/Teams chats – essentially extending your email phishing filters to these collaboration platforms to catch bad messages in real time.
Q5: What are some tips to prevent phishing in Slack or Teams?
Treat Slack and Teams messages with the same caution as you do emails. Double-check any unexpected request (for passwords, money transfers, gift cards, etc.) by confirming through another channel or with the person directly before you act. And if a chat message contains a strange link or file, pause and verify it’s legit before clicking. A little extra skepticism – and regular security reminders for your team – goes a long way in keeping your workspace safe.
Q6: Do Slack and Teams have built-in phishing protection?
They have some basic safety features, but nothing as advanced as dedicated email filters. Slack, for example, keeps random outsiders out by default, and Microsoft Teams lets you block or screen messages from unknown people. However, determined attackers can still slip through those cracks (for instance, by hijacking a trusted account), so adding extra security measures – and staying vigilant – is still important.
Subscribe to Our Newsletters!
Be the first to get exclusive offers and the latest news
Don’t let legacy tools leave you exposed.
Tomorrow's Threats. Stopped Today.






.svg)