Global Hybrid AI Phishing Scam: Luxury Cars, Job Portals & Phone Fraud

Why does this matter?
Real, legitimate websites can be compromised to deceive users into falling victim to wire transfer fraud, credit card theft, and data harvesting. These attacks start by bypassing security controls and end up in a user’s inbox.
StrongestLayer's Discovery
StrongestLayer recently uncovered an extensive network of deceptive, AI-generated websites operated by a sophisticated phishing group. These sites include:
- Fake luxury car dealerships
- Job boards
- DevSecOps HR portals
- Real estate agencies
- Numerous other fictitious brands
All of these are targeting users across the US, EU, Middle East, and Africa.





This story echoes a previous blog where our team uncovered around 3 million domains involved in a similar scenario. However, this time, there are some notable differences.
The campaign was exposed by several telltale signs including (but not limited to) the use of already known and identical phishing site templates, exactly same contact page templates, identical contact details used across many of these websites and the attackers’ reuse of the same contact details, including the same VoIP scam phone number and in some cases, even the same generic email address “contact@company.com.” which the attackers typically left unchanged to hone in on novice targets and to potentially remain under the radar.
The StrongestLayer Threat Intelligence team also identified a key difference this time: alongside the fake brands, legitimate brand websites were compromised to host fake contact pages containing the same templates and fraudulent details. Although some administrators have since cleaned up their sites after the breach, the Google search engine cache still reflects the malicious content due to recent crawling by search spiders.


One example is the car sales website Boutique Auto Haus. While the business is legitimate and operates in New Jersey, attackers have compromised the website by adding a fake contact page. This page redirects visitors to the attackers’ phone number.
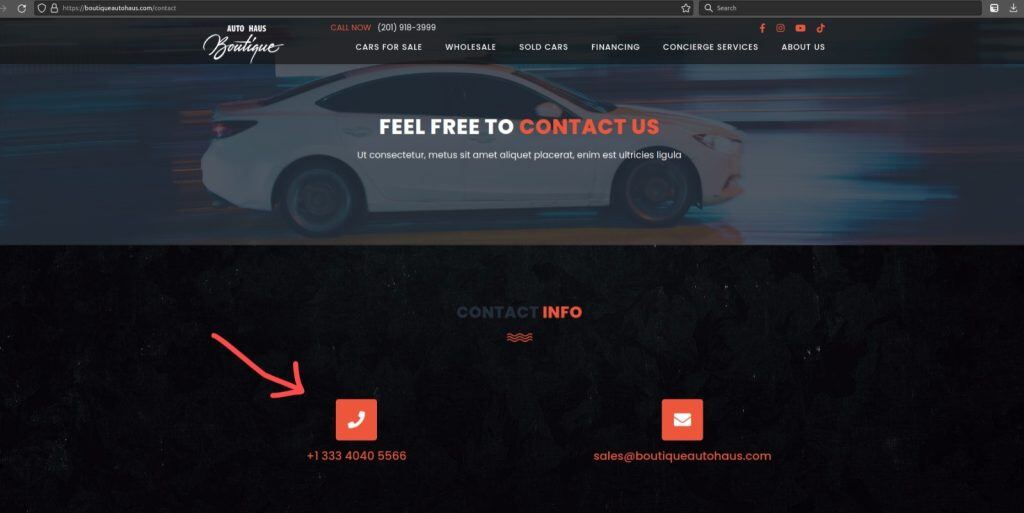
By compromising legitimate websites, the phishing group isn’t just relying on their own fake brands; they’re also leveraging established brands to redirect traffic to their fraudulent contact forms for malicious data collection purposes. Here’s another example:


This large-scale phishing operation, characterized by its global reach, sophisticated fake website templates, and the compromise of legitimate sites, underscores the advanced technical expertise of the threat actors. Their ability to hijack legitimate websites and embed fake contact pages highlights the operation’s sophistication and their capability to execute online fraud on a global scale.
Below is a sample list of IOCs, fake brands and compromised websites still being exploited in this operation:
Subscribe to Our Newsletters!
Be the first to get exclusive offers and the latest news
Don’t let legacy tools leave you exposed.
Tomorrow's Threats. Stopped Today.






.svg)