The Security Paradox: Why "More Protection" Is Creating New Vulnerabilities

In the modern enterprise, security teams are winning the battle for "compliance" but losing the war for "safety." New research conducted by StrongestLayer, analyzing over 15,000 industry respondents across 15 global surveys, reveals a disturbing trend: The Security Paradox.
The paradox is simple yet devastating: As organizations layer on more security tools—stricter email filters (SEGs), heavier VPNs, and aggressive DLP agents—they inadvertently increase "friction" for employees. This friction does not stop risky behavior; it merely drives it underground.
Our data shows that 61% of employees are dissatisfied with their corporate technology, leading to a projected 75% adoption rate of Shadow IT by 2027. Furthermore, the culture of "blame" has created a Silence Spiral, where 50% of employees are too afraid to report security mistakes, leaving organizations blind to active breaches.
This report breaks down the hidden costs of "strict" security—from the epidemic of False Positives to the psychological erosion of trust—and offers a roadmap for a new, context-aware approach that aligns security with the speed of business.
The Failure of the "Castle and Moat"
For the last two decades, cybersecurity strategy has been defined by a single metaphor: The Castle.
The logic was straightforward. If we build higher walls (Firewalls), dig deeper moats (VPNs), and guard the gate more aggressively (Email Gateways), we will keep the bad guys out. We treated the enterprise like a fortress and the employees like the villagers we were protecting.
But in 2026, the Castle model collapsed.
The modern workforce is not inside the castle. They are remote, mobile, and distributed. They are working from coffee shops in Singapore, home offices in London, and coworking spaces in New York. They are using SaaS applications (Salesforce, Slack, Zoom) that live in the cloud, not in your data center.
When we try to apply "Castle" security to a "Cloud" world, we create Friction.
- We force traffic through slow VPN concentrators.
- We block legitimate files because they "look" suspicious.
- We quarantine critical business emails because the sender's domain is new.
The result? The "villagers" are revolting. They aren't trying to destroy the castle; they are just trying to do their jobs. But to do so, they are bypassing the guards.
This report is not about "Hackers" or "Malware." It is about the Operational Reality of security. It is about what happens when your security policies collide with human nature.
Part 1: The Methodology (Validating the Crisis)
Before we dissect the failure of modern security policies, we must validate the data. In an industry full of vendor-sponsored "fluff," this report stands apart because of its scope.
The Dataset
We did not just ask 100 CISOs what they thought was happening. We aggregated insights from 15,000 respondents across the globe. This dataset provides a rare 360-degree view of the enterprise.
- The Sample: A diverse mix of CIOs, CISOs, IT Directors, and—crucially—non-technical end users.
- The Demographics:
- 35% IT & Security Professionals (The Enforcers).
- 25% DevOps & Engineering (The Builders).
- 20% C-Suite & Leadership (The Decision Makers).
- 20% General Knowledge Workers (The Users).
Why This Matters
Most security reports suffer from "Survivorship Bias." They only analyze the threats that were caught. They don't analyze the threats that were ignored or the policies that were bypassed. By surveying the end-users—the marketing manager trying to send a large file, the sales director waiting for a contract—we have uncovered the Hidden Cost of Security.
Part 2: The "False Positive" Epidemic
Why "Safe" is the New "Broken"
If you ask a legacy security vendor what their success metric is, they will say: "We blocked 99.9% of threats."
But if you ask a CEO what their success metric is, they will say: "We closed the deal."
These two metrics are currently at war. The most immediate finding from our research is that legacy security tools are too aggressive. The #1 frustration cited by leadership is not "phishing attacks"—it is "Missing Emails Due to False Positives."
The 40% Statistic
Our data reveals that 40% of CIOs receive frequent, high-priority complaints about legitimate business emails being blocked by their Secure Email Gateway (SEG).
The Anatomy of a False Positive
Why is this happening? Why can't billion-dollar security tools tell the difference between a hacker and a client?
- New Domain Penalties: A startup or new vendor registers a domain (e.g., new-vendor.com). Because the domain is less than 30 days old, the SEG scores it as "High Risk" and blocks all emails.
- Strict SPF/DKIM Failures: A legitimate marketing newsletter is sent via Mailchimp but has a slight misconfiguration in its DMARC record. The SEG blocks it entirely.
- Keyword Triggering: A legal contract contains terms like "Wire Transfer" or "Urgent Payment." The SEG sees these as "Business Email Compromise (BEC)" indicators and quarantines the email.
The Business Consequence
When a security tool blocks a legitimate email, it isn't just a technical glitch; it's a business failure.
- Revenue Loss: If a sales contract is flagged as "Spam," the deal stalls. The competitor who uses a less restrictive filter gets the contract.
- Vendor Friction: Procurement emails from new suppliers often trigger strict filters, causing supply chain delays.
- The "Boy Who Cried Wolf" Effect: When employees constantly see "Warning: External Sender" banners on safe emails, they develop "Banner Blindness." They stop reading the warnings entirely. This means when a real phishing attack arrives, they ignore that banner too.
A "False Positive" in cybersecurity occurs when a security system incorrectly identifies benign activity as malicious. In 2026, false positives are the primary driver of friction between Security Operations Centers (SOC) and business units, often leading to the adoption of "Shadow IT" communication channels.
Part 3: The Shadow IT Explosion (2022–2027)
The Inevitable Result of Friction
When the "official" way of working is broken (slow VPNs, blocked files, quarantined emails), employees do not stop working. They simply find a new way to work.
This is the birth of Shadow IT.
The Growth Curve: 41% to 75%
Our research tracks the adoption of unauthorized SaaS applications over a 5-year period. The trend line is undeniable and accelerating:
- 2022: 41% of employees used Shadow IT.
- 2024: 53% of employees used Shadow IT.
- 2026 (Today): ~60% usage.
- 2027 (Projected): 75% of employees will use unapproved tools to do their jobs.
The "Rational Actor" Theory
Security teams often view Shadow IT as "Reckless Behavior." Our data suggests it is actually "Rational Behavior."
Consider this scenario:
- The Task: A marketing manager needs to send a 5GB video file to a client for a campaign launch tomorrow.
- The Corporate Tool: The official email limit is 25MB. The sanctioned secure file transfer tool requires a VPN login, has a confusing interface, and takes 2 hours to upload.
- The Shadow Solution: The manager uploads the file to their personal Dropbox or WeTransfer in 30 seconds.
- The Outcome: The client gets the video. The campaign launches on time. The manager gets a bonus.
- The Security Gap: That file—containing sensitive IP—is now outside the corporate perimeter. The SOC cannot see it, scan it, or delete it.
The Hard Truth: Shadow IT is a rational economic response to bad IT policy. If you make security hard, you make insecurity inevitable. By 2027, if your security tools are not as frictionless as consumer apps, they will be bypassed by 75% of your workforce.
Part 4: The Top 10 Employee Frustrations
Where Security Experience (SX) Fails
We asked our 15,000 respondents to rank the specific "friction points" that make them hate their corporate security. These are the barriers that drive the Shadow IT explosion.
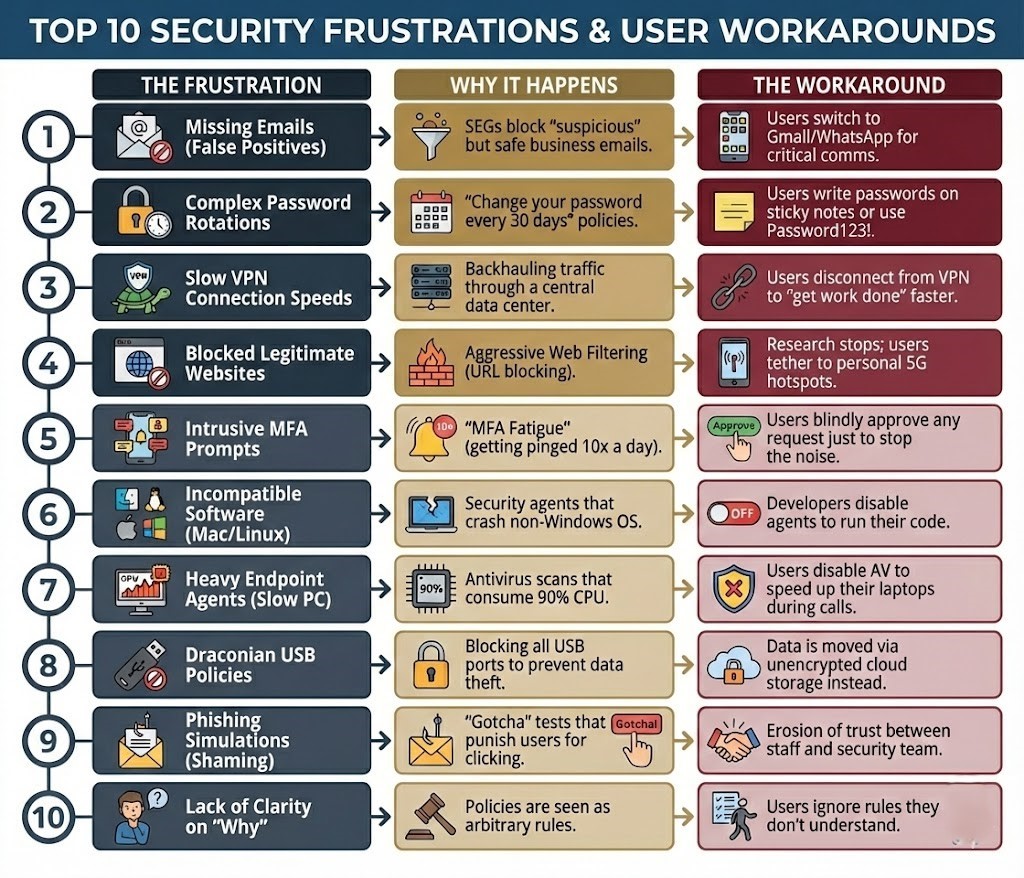
Deep Dive: The VPN Problem
Rank #3 (Slow VPNs) is a critical infrastructure failure. Traditional VPNs were designed when 90% of traffic was internal (Employee ⇒ Data Center). Today, 90% of traffic is external (Employee ⇒ Internet/SaaS).
Forcing a Zoom call to travel from a user's home ⇒ Corporate VPN ⇒ Internet ⇒ Zoom Server adds massive latency.
- The User Reaction: "The VPN makes Zoom lag. I'll turn it off."
- The Result: The user is now browsing the open internet with zero protection.
Part 5: The "Silence Spiral" (The Culture of Fear)
Why 50% of Breaches Go Unreported
This is perhaps the most critical finding in the entire "Hidden Cost of Security" report. It is not a technology problem; it is a psychological problem.
The Statistic: 50% of employees fear negative repercussions if they report a security mistake.
The Anatomy of a Cover-Up
Imagine an employee clicks a link in an email. A second later, they realize, "Oh no, that looked fake."
Scenario A: The Fear Culture (Current State)
- The Thought Process: "If I tell IT, they will yell at me. They will make me retake that boring 1-hour training video. My boss will find out and it might affect my performance review."
- The Action: They close the browser and say nothing.
- The Result: The malware (Ransomware/Trojan) silently installs in the background. It dwells for weeks, escalating privileges and stealing data. By the time the SOC detects it, the damage is catastrophic.
Scenario B: The Psychological Safety Culture (Desired State)
- The Thought Process: "I made a mistake. But I know the security team is here to help, not punish. If I tell them now, they can fix it fast."
- The Action: They click the "Report Phishing" button immediately.
- The Result: The SOC isolates the machine within 5 minutes. No data is lost. The employee is thanked for their speed.
The Failure of "Phish Testing"
For a decade, the industry has relied on simulated phishing campaigns to "train" employees.
- You send a fake email.
- The employee clicks.
- You show a scary "YOU FAILED" screen.
- You assign them mandatory training.
Our data suggests this has backfired. Instead of teaching employees how to spot threats, it has taught them to fear the security team. When 50% of your workforce is afraid to talk to you, you don't have a security program; you have a surveillance program. You have blinded yourself to the most valuable sensor network you have: your people.
Part 6: The Solution (Context-Aware Security)
Moving From "No" to "How"
We cannot solve the Security Paradox by adding more blocking rules. We must shift the paradigm from Static Security to Context-Aware Security.
The goal is not to lower the walls, but to make the gates smarter.
1. Solve False Positives with Behavioral AI
Legacy SEGs use "Signature Detection" (Is this IP bad? Is this keyword bad?). This is prone to error.
- The Future: Use LLM-driven behavioral analysis.
- How it works: Instead of looking for "bad" keywords, the AI learns the "normal" behavior of your vendors. Does this email sound like the CFO? Is this invoice format typical for this supplier?
- The Benefit: StrongestLayer’s approach reduces False Positives by understanding intent, ensuring business flows continue uninterrupted.
2. Embrace "Sanctioned" Shadow IT
You cannot block 75% of the internet. If you try to block Dropbox, users will find Box. If you block Box, they will use Google Drive.
- The Fix: Instead of blocking the tool, secure the data.
- Technology: Use Browser Isolation and CASB (Cloud Access Security Broker) tools. Allow employees to use the productivity tools they love, but wrap those sessions in a secure layer that prevents data exfiltration (e.g., "You can upload to Dropbox, but you cannot upload files tagged 'Confidential'").
3. Build a "Reporter's Immunity" Policy
To break the Silence Spiral, organizations must guarantee immunity for self-reporting.
- The Policy: "If you report a mistake you made (clicked a link, lost a drive) within 1 hour, there will be zero disciplinary action."
- The Incentive: Gamify the reporting. Give "Security Champion" badges or small rewards to employees who report active threats.
- The Result: You turn your 15,000 employees into 15,000 active defenders.
Part 7: Future Outlook (2027 and Beyond)
The trajectory is clear. The "Security Paradox" will either be the catalyst for change, or the cause of the next great data breach.
By 2027, we predict a bifurcation in the market:
- The "Fortress" Companies: They will continue to lock down endpoints, block websites, and punish employees. They will see Shadow IT usage spike to 90%, and they will suffer from massive, silent breaches caused by "Shadow" vectors they cannot see.
- The "Fluid" Companies: They will adopt Context-Aware Security. They will accept that employees use SaaS tools and personal devices. They will use AI to monitor behavior rather than infrastructure. They will have lower friction, higher productivity, and—ironically—better security.
StrongestLayer is building for the Fluid future. We believe that the best security is the kind you don't notice until you need it.
Final Thoughts
The era of the "Department of No" is over.
As we move toward 2026, the metrics of success for a CISO are changing. It is no longer about "How many threats did we block?" It is about "How fast did we allow the business to run safely?"
The data from our 15,000 respondents is a wake-up call: Friction is the enemy.
If we continue to treat employees as the "weakest link" and subject them to 40% false positives and punitive policies, they will continue to bypass us. But if we align security with productivity—using intelligent, invisible layers of protection—we can finally close the gap on Shadow IT and build an enterprise that is both fast and secure.
Major Data Sources
- ThinkCyber Security Awareness Survey (n=163 cybersecurity professionals, 2024)
- TalentLMS Workplace Compliance Survey (n=1,000+ US employees, 2025)
- Gartner Shadow IT Research (2022-2023)
- JumpCloud Shadow IT Survey (2024)
- Capterra SMB Study (n=300 IT professionals and project managers, 2023)
- Robert Half Technology CIO Survey (n=1,400 CIOs)
- Bitdefender Security-Productivity Research (2024-2025)
- University of Chicago/UCSD Security Training Study (n=15,000+ employees, 2024-2025)
Rankings based on measured operational impact, adoption of circumvention behaviors, and organizational scope of effect. Research conducted December 2025 - January 2026.
Frequently Asked Questions (FAQ)
Q1: What is the Security Paradox?
The Security Paradox is a cybersecurity phenomenon where the implementation of stricter security controls (such as aggressive email filtering, complex password policies, and VPNs) inadvertently decreases overall organizational safety. This occurs because high-friction policies force employees to bypass security protocols using unauthorized tools ("Shadow IT"), leaving the organization blind to new risks.
Q2: How common is Shadow IT in 2026?
According to StrongestLayer's 2026 research, Shadow IT usage is currently at 60% and is projected to reach 75% by 2027. This represents a massive increase from just 41% in 2022, driven largely by employee dissatisfaction with corporate IT tools.
Q3: Why do employees bypass security protocols?
The primary driver of security bypass is productivity friction. Our data shows that 61% of employees are dissatisfied with the technology provided by their IT departments. When security tools block legitimate work (False Positives) or slow down connections (VPN latency), employees behave rationally and switch to personal devices or unauthorized apps to meet their deadlines.
Q4: What is the business impact of false positives in email security?
False positives—when a security tool incorrectly blocks a safe email—are the #1 frustration for CIOs in 2026. 40% of IT leaders report that false positives disrupt critical business operations, leading to lost revenue, delayed contracts, and supply chain friction.
Q5: Why is the "Silence Spiral" dangerous for cybersecurity?
The "Silence Spiral" refers to a culture where employees are afraid to report security mistakes (like clicking a phishing link) due to fear of punishment or shaming. Research shows that 50% of employees fear repercussions for reporting errors. This is dangerous because it leads to "silent breaches," where malware dwells undetected in a network for weeks because the only witness—the employee—was too terrified to speak up.
Subscribe to Our Newsletters!
Be the first to get exclusive offers and the latest news
Don’t let legacy tools leave you exposed.
Tomorrow's Threats. Stopped Today.






.svg)