
Direct Send Deception: How a Microsoft 365 Exploit Fuels Hyper-Personalized Credential Theft

A collaborative analysis between StrongestLayer's TRACE AI and Jeremy, a Security Lead at a large electronics company
- Joshua Bass, CPO at StrongestLayer
- Riz, CTO at StrongestLayer
- Jeremy, Security Engineer at a large electronics company
- Mudassar Hassan, Detection Lead at StrongestLayer
Introduction
When StrongestLayer's advanced AI "TRACE" flagged what appeared to be a simple voicemail notification as malicious, we knew we had uncovered something significant. But it wasn't until we partnered with Jeremy, a seasoned Security Architect at a major manufacturing company, that the full sophistication of this attack became clear.
Jeremy's Perspective: "When Josh from StrongestLayer called about the suspicious emails his system had detected, I was initially skeptical. The headers didn't make sense for what should have been internal communications. But as we dug deeper, we realized we were looking at something far more dangerous than a typical phishing attempt – this was a targeted exploitation of Microsoft 365's Direct Send feature that could fool even experienced security professionals."
This blog post chronicles our joint investigation into a sophisticated, multi-layered spear phishing attack that leverages Microsoft 365 Direct Send exploitation, advanced obfuscation, and dual-payload delivery to steal user credentials with a dangerous twist: deep personalization designed to disarm even the most cautious users.
Part 1: The Discovery – When AI Meets Human Expertise
StrongestLayer's Detection
Our TRACE AI immediately identified several red flags in what appeared to be routine voicemail notifications. The system flagged the emails based on header anomalies, authentication failures, and behavioral patterns that didn't match legitimate communications.
Jeremy's Investigation Begins
Jeremy: "Initially, we thought we were dealing with a standard spoofing attempt. But when I started analyzing the headers, something didn't add up. These emails were coming through our own mail protection systems, appearing as internal traffic, yet failing basic authentication checks. That's when I realized we might be looking at a Direct Send exploitation."
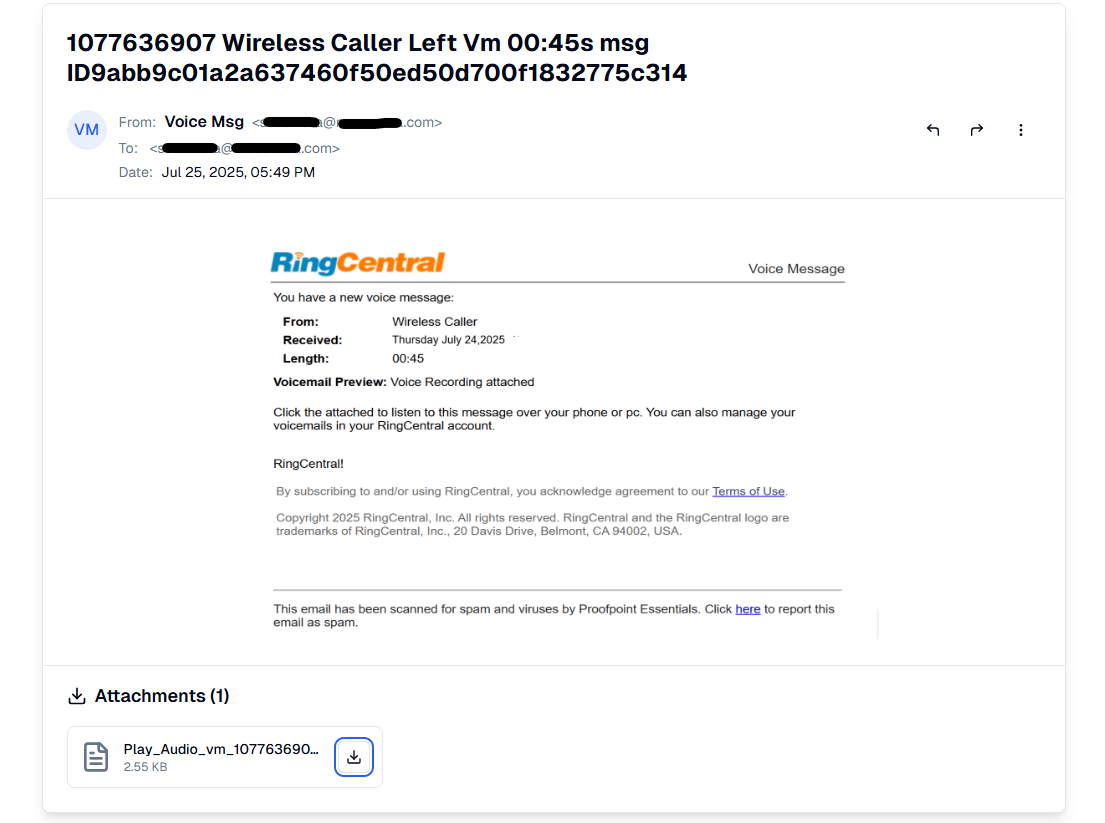
The attack begins with emails that look like legitimate voicemail notifications from trusted services like RingCentral. The subject lines create urgency, and the body prompts users to open attachments to hear messages.
The Forensic Evidence
Working together, we identified key indicators in the email headers that revealed this wasn't legitimate, authenticated email traffic:
StrongestLayer Analysis: Our AI detected patterns consistent with spoofed communications:
- Authentication failure across all three key checks (SPF, DKIM, DMARC)
- Suspicious relay paths from generic hosting providers
- Behavioral anomalies in sender patterns
Jeremy's Field Notes: "What made this particularly concerning was the use of our own smart host (company.mail.protection.outlook.com) to deliver these messages. The emails were failing SPF and DMARC checks, but because they came through our internal smart host via Direct Send, they were being treated as trusted internal traffic. This is exactly the kind of sophisticated attack that requires both automated detection and human analysis to fully understand."
Key forensic indicators included:
- Authentication Failures: SPF softfail/fail from unauthorized IPs, DKIM signatures missing (dkim=none), and DMARC failures
- Suspicious Origins: IP addresses from generic hosting providers in the US and Israel
- Direct Send Indicators: Mail paths showing unauthenticated submission through SmtpServer.Submit
Part 2: The Lure – Bypassing Traditional Defenses
StrongestLayer's AI Analysis
The attack's evasiveness centered on its presentation – no analyzable text for traditional scanners, just a single, high-fidelity inline image designed to perfectly mimic legitimate service notifications.
Jeremy's Response Strategy: "When I saw that the entire lure was contained within images, I knew we were dealing with attackers who understood how to bypass NLP and keyword-based filters. This is where having both AI detection and human expertise becomes crucial – the AI caught what the image was trying to accomplish contextually, while we could implement immediate containment measures."
The Technical Breakdown
By placing call-to-action messages ("You have a new voice message") inside images, the attackers bypassed many traditional text-based security filters. Users saw convincing visual prompts with only one instruction: open the attachment.
Collaborative Insight: While legacy systems might miss image-based content, our combined approach – AI contextual analysis plus human forensic investigation – identified the attack pattern: failed authentication + social engineering theme + external file dependency = high-risk threat.
Part 3: The Payload Analysis
Dual-Vector Attack Discovery
Jeremy's Investigation: "We identified two distinct payload types in this campaign – HTML files and SVG files. Both were using sophisticated obfuscation techniques that required careful analysis to fully understand their capabilities."
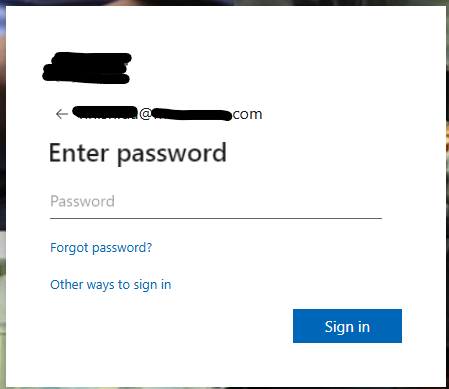
Vector 1: The HTML Credential Harvester
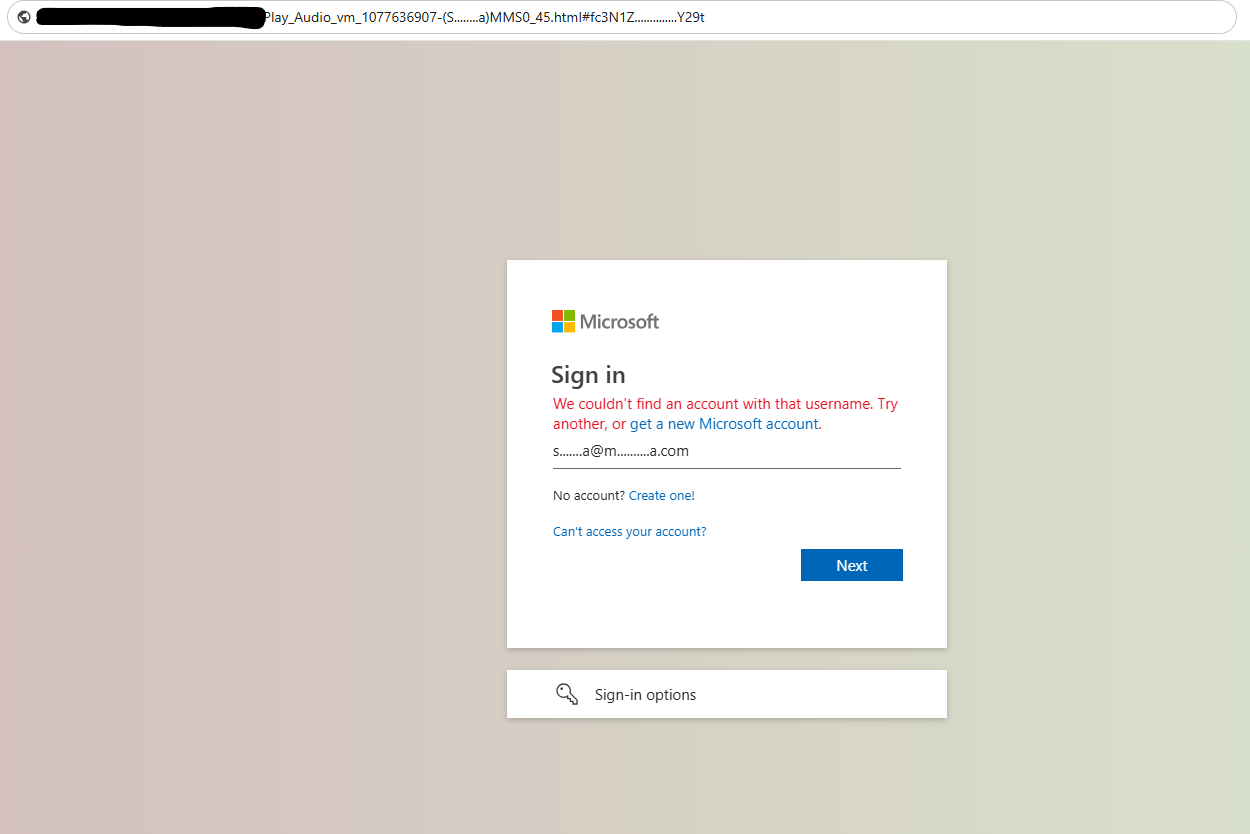
The primary payload appeared as harmless HTML files named "Play_Audio_vm_...html". Instead of playing voicemails, these files launched multi-layered credential harvesting attacks.
StrongestLayer Detection: Our AI identified the obfuscation patterns and suspicious JavaScript execution chains before users could interact with the payloads.
Jeremy's Technical Analysis:
<html>
...
<body>
<img src="#" onerror="(new Function(atob(this.dataset.scolding)))()"
data-scolding="[Base64-encoded malicious script]"
data-patrol="[Base64-encoded victim email]">
</body>
</html>
"The attack used a clever three-step process: an invalid image tag triggers an onerror event, which Base64-decodes and executes hidden JavaScript, which then fetches the actual phishing page from a remote server. This multi-stage approach made it much harder to detect and analyze using traditional methods."
Vector 2: The SVG Backup Plan
Jeremy: "The SVG variant was particularly concerning because many security filters treat .svg files as safe images, not realizing they can execute JavaScript. This shows the attackers had multiple vectors prepared."
The malicious SVG structure:
<?xml version="1.0" encoding="UTF-8" standalone="no"?>
<svg ...>
<script type="application/ecmascript"
xlink:href="data:application/ecmascript;base64,[encoded payload]"/>
</svg>
Collaborative Analysis: The SVG payload used similar obfuscation techniques but with additional custom encoding layers designed to defeat automated analysis systems.
Part 4: The Personalization Factor
What Made This Attack Particularly Dangerous
Jeremy's Key Observation: "What elevated this from a standard phish to a truly dangerous spear phishing attack was the hyper-personalization. The JavaScript didn't just render a generic login page – it dynamically pulled our company logo and official branding to create a perfectly legitimate-looking credential harvesting page. When employees saw their own corporate branding, their guard naturally dropped."
StrongestLayer's AI Perspective: Our system detected not just the technical attack vectors, but also the behavioral patterns indicating reconnaissance and personalization – key indicators of advanced persistent threats.
The attack used victims' email addresses to:
- Pre-fill login forms
- Dynamically fetch corporate logos and branding
- Create company-specific phishing pages
- Establish false trust through familiar visual elements
Part 5: The Complete Attack Chain
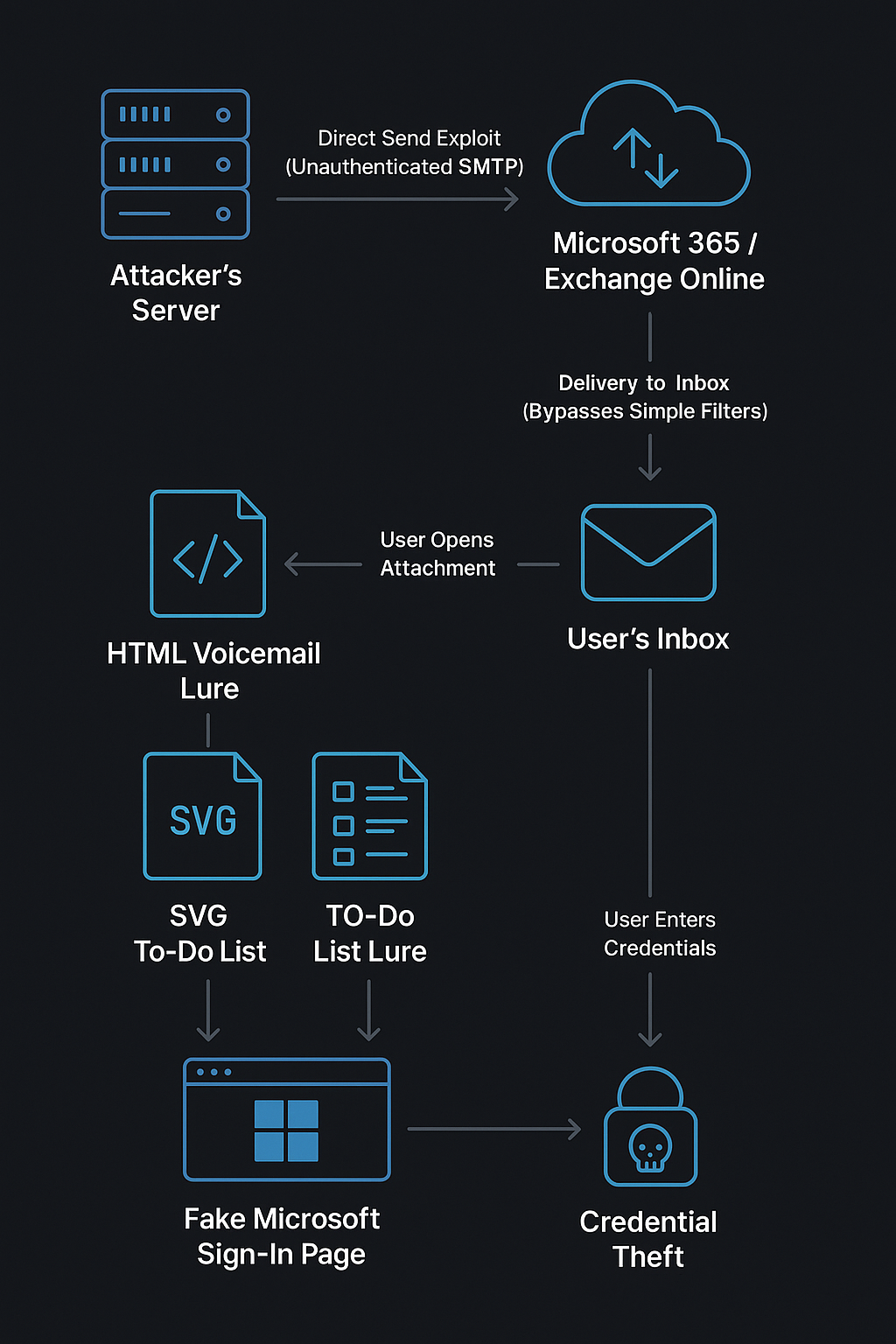
Collaborative Timeline Reconstruction:
- Initial Compromise: Attackers use PowerShell and Direct Send to bypass authentication
- Delivery: Image-based lures evade text analysis
- Engagement: Obfuscated payloads in HTML/SVG files
- Personalization: Dynamic branding harvesting
- Credential Theft: Sophisticated phishing page deployment
Jeremy's Implementation Notes: "Understanding this complete chain was crucial for our response. We couldn't just block the immediate threat – we had to address the underlying Direct Send vulnerability and implement monitoring for similar attack patterns."
Part 6: Defense and Mitigation
Immediate Response Measures
Jeremy's Defensive Strategy: "We implemented a multi-layered approach while Microsoft developed their official mitigation. We used header stamping at our mail gateway – adding a custom header that gets checked on the M365 side. If the header doesn't exist, the email gets quarantined. This method has been working well as a temporary solution."
StrongestLayer's Recommendations: Our AI-driven analysis supports several key defensive measures:
- Header Analysis Enhancement: Direct Send exploitation is detectable through careful header analysis
- File Type Restrictions: Treat all HTML and SVG attachments from external senders as high-risk
- Authentication Enforcement: Implement strict DMARC policies (p=reject)
- Behavioral Monitoring: Monitor for spoofed internal emails and authentication anomalies
Microsoft's New Mitigation
Collaborative Update: Microsoft recently introduced the "Reject Direct Send" setting in Exchange Admin Center (April 2025), directly addressing this vulnerability.
Jeremy: "We're planning to implement Microsoft's new setting as soon as we can fully test it in our environment. However, the header stamping method we developed provides an immediate solution that other organizations can implement while waiting for the official fix."
Conclusion: The Power of Collaborative Security
Jeremy's Final Thoughts: "This investigation really highlighted how modern threats require both advanced AI detection and human expertise. StrongestLayer's TRACE AI caught what our traditional filters missed, but it took human analysis to understand the full scope and develop effective countermeasures. It's this kind of collaboration between security vendors and practitioners that makes the difference in staying ahead of sophisticated attacks."
StrongestLayer's Perspective: This campaign demonstrates why siloed security tools fail against advanced threats. The attackers designed their tactics to defeat individual security measures one by one: Direct Send exploitation to bypass sender authentication, image-based content to evade text scanners, and obfuscated code to bypass file-type filters.
Key Takeaways for Security Teams:
- Embrace Collaborative Detection: AI-driven analysis combined with human expertise provides the most comprehensive threat detection
- Focus on Attack Chains: Understanding complete attack methodologies enables better defensive strategies
- Implement Defense-in-Depth: Multiple detection layers are essential for catching sophisticated, multi-stage attacks
- Share Intelligence: Cross-organization collaboration accelerates threat understanding and mitigation development
- Monitor Direct Send Usage: If you're not actively using Direct Send, disable it immediately
Jeremy: "Don't assume that internal means safe. This attack showed us that sophisticated threat actors are finding ways to abuse legitimate features in ways that can fool even experienced security professionals. Constant vigilance and collaborative defense are more important than ever."
For security teams interested in discussing Direct Send mitigation strategies or similar threat investigations, both StrongestLayer and security practitioners like Jeremy are committed to advancing collective cybersecurity defense through knowledge sharing and collaboration.
Try StrongestLayer Today










.png)







.png)































%20Attacks%20in%202025.jpg)









